Safe Routes, Safer Data: Securing TMS in the Digital Supply Chain

Table of Contents
In a Hurry? Here's the Security Snapshot
- Transportation Management Systems (TMS) hold sensitive shipping and customer data.
- Data breaches can cost millions and damage brand trust.
- Secure TMS systems should include encryption, user role controls, and regular audits.
- Businesses in MENA must align with local data laws (e.g., UAE’s PDPL, KSA’s PDPL).
- AI and real-time tracking require layered cybersecurity protocols.
- Strong vendor vetting, cloud security, and staff training are essential.
- Omniful TMS integrates security with performance — from real-time tracking to driver logs.
- Protecting logistics data today secures tomorrow’s supply chain resilience.
Why Data Security in TMS Shouldn’t Be an Afterthought
In the world of logistics, information moves as fast as goods. Behind each shipment is a trail of sensitive data — customer addresses, route schedules, fleet locations, and commercial invoices. A modern Transportation Management System (TMS) acts as the digital hub for this data. Yet, with rising cyber threats, securing your TMS is no longer optional — it's critical.
Whether you're delivering perfumes across Riyadh or groceries across Dubai, the potential fallout from data breaches includes financial loss, legal trouble, and lost customer trust. And with TMS systems now integrating real-time fleet tracking, delivery zones, and AI-powered automation, the security stakes have never been higher.
The Data a TMS Collects: A Hacker’s Jackpot
Modern TMS platforms collect and process vast quantities of operational and personal data:
- Customer Details: Names, phone numbers, addresses.
- Shipment Information: Content, weight, origin, destination.
- Route Plans: Optimised delivery paths, geofencing triggers.
- Fleet Data: Driver ID, vehicle GPS, fuel consumption.
- Payment & Cash Ledger Data: Especially important in COD-heavy regions.
This data not only powers delivery speed and efficiency, but also becomes an attractive target for cyber attackers. A single weak point in the system could expose thousands of data records in seconds.
Key Security Risks in Transportation Management Systems
As businesses scale, so do their vulnerabilities. Common risks that plague TMS systems include:
Poor Access Control
Without defined user roles and permissions, unauthorised access can lead to data leakage or manipulation.
Outdated Software
Legacy TMS solutions often lack security patches, exposing networks to ransomware and malware.
Cloud Misconfigurations
With the rise of cloud-hosted platforms, misconfigured cloud environments create major security loopholes.
Weak API Security
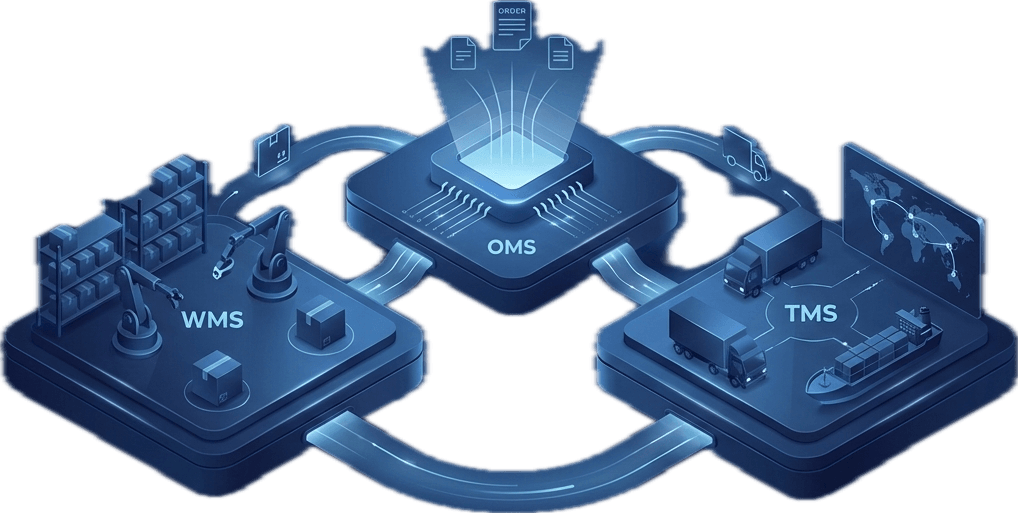
Many TMS platforms integrate with OMS, WMS, and other solutions. Insecure APIs can expose sensitive operations to external threats.
Human Error
The simplest but most dangerous vector. Phishing emails, poor password hygiene, or misuse of admin rights can result in massive breaches.
Security Features Your TMS Must Include
Here are the non-negotiables for a secure TMS solution, especially for MENA-based businesses:
Role-Based Access Management
Every user — from the fleet manager to the driver — should only access what they need. Omniful’s TMS allows full access control down to the hub and brand level.
End-to-End Encryption
Encrypt both data at rest and in transit using protocols like TLS 1.3 and AES-256 to protect against eavesdropping and interception.
Audit Logs
Enable comprehensive activity tracking and timestamping of user actions. This supports both accountability and forensic investigations after incidents.
API Security
Use OAuth2, rate limiting, and encryption to secure third-party integrations with OMS, Warehouse Management System, and Order Management System.
Multi-Factor Authentication (MFA)
Require users to verify identity with a second device or biometric data for login.
Region-Specific Regulations: A Must for MENA Businesses
As digital supply chains grow in the Middle East, local data regulations are becoming stricter. Compliance is not only ethical — it’s legal.
Saudi Arabia
The Personal Data Protection Law (PDPL), enforced by the SDAIA, mandates explicit user consent and secure storage of personal data.
United Arab Emirates
The UAE Federal Law No. 45 of 2021 requires clear data processing frameworks, breach notification protocols, and local data hosting.
Non-compliance could lead to penalties or blacklisting, particularly when dealing with government contracts or B2B partners in sensitive sectors.
Real-World Example: Why TMS Security Matters
Consider the case of a large GCC-based e-commerce firm whose last-mile delivery software lacked user segmentation. One compromised admin account led to:
- Theft of 60,000 customer records.
- Exposure of route schedules and cash collection points.
- Delays in last-mile delivery due to manual fallback procedures.
The company faced legal consequences and brand damage, all of which could’ve been avoided by using a TMS with strong data privacy controls.
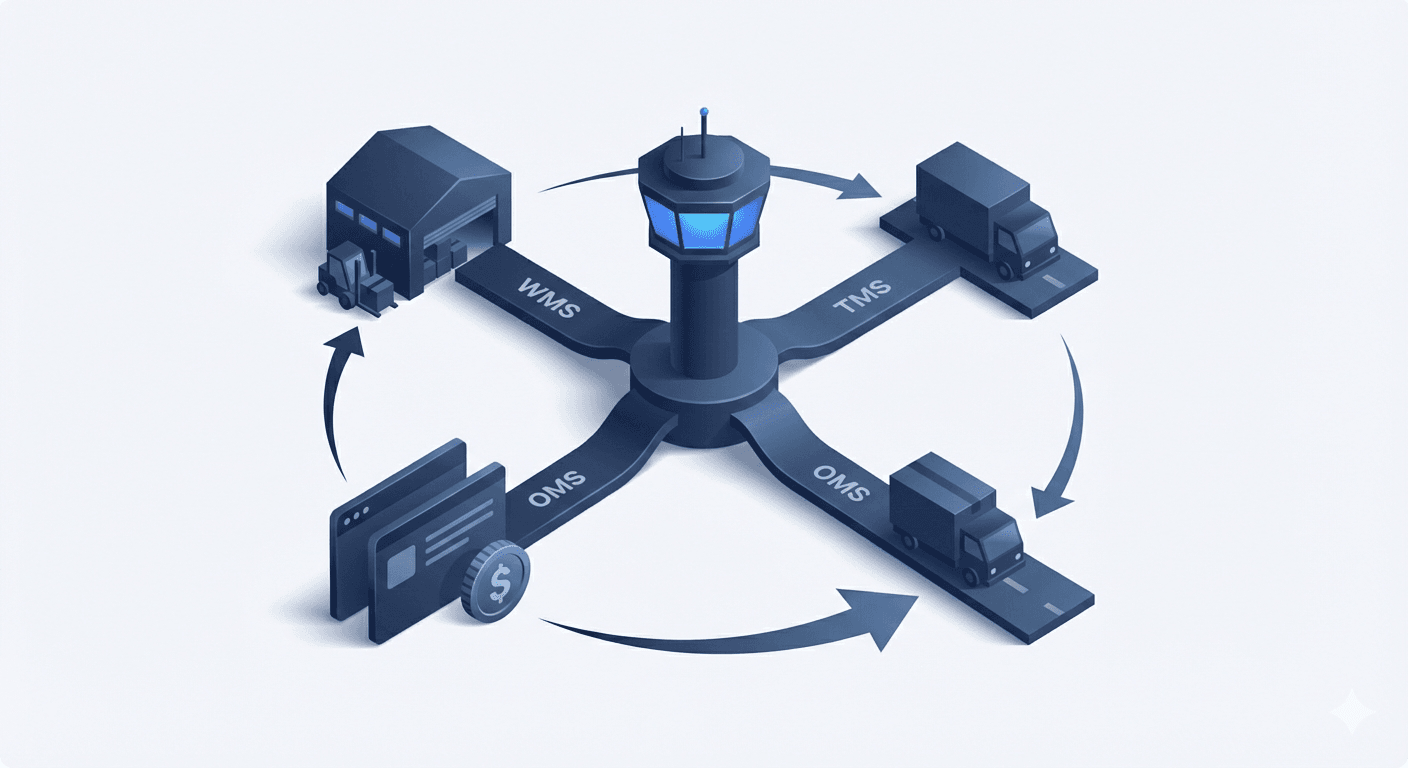
Omniful TMS: Built Secure, Designed for Scale
Omniful’s Transportation Management System addresses security at every layer:
- Real-time Tracking: GPS data is encrypted during transfer to protect driver locations.
- Driver Management: Secure profiles and logs restrict access to route details.
- API Integrations: Seamless and safe data exchange with Omniship, Shipping Gateway, and others.
- Role Control: Create unlimited user roles with permission-based access.
- Cash Ledger: Track and secure every cash transaction in COD workflows.
These features support not only data protection, but also operational resilience in fast-moving supply chains.
Best Practices to Strengthen Your TMS Data Privacy
Securing your TMS isn’t just about technology. It also involves process design, vendor accountability, and team awareness. Consider these steps:
-
Run Penetration Tests Quarterly
Identify weaknesses before malicious actors do. -
Train Staff Regularly
Security awareness can reduce human error. -
Use Reputable Vendors
Choose providers with proven compliance and strong incident response systems. -
Limit Third-Party Access
Vet all plugins or modules integrated into your TMS. -
Enable Geofencing Alerts
Be notified of unusual movements or access from unauthorised locations.
Integrating Across the Stack: Securely and Seamlessly
Today’s TMS must integrate with several other critical tools:
Every connection is a potential risk. Omniful’s platform ensures all integrations follow secure communication standards, like API key rotation and IP whitelisting.
The Future: AI and the Need for Proactive Security
With AI route optimisation and predictive logistics models becoming mainstream in TMS systems, data privacy goes beyond compliance — it becomes a competitive edge.
AI requires large volumes of route and driver data. That means stronger encryption, anonymised data modelling, and more frequent data governance audits.
As fleets grow and automation deepens, expect a future where TMS vendors will need certifications such as ISO/IEC 27001 or even GDPR-aligned data controls for cross-border commerce.
Frequently Asked Questions
Is a cloud-based TMS more secure than an on-premise one?
Yes, if properly managed. Cloud TMS vendors often offer built-in redundancy, encrypted backups, and 24/7 security monitoring.
What happens if a driver’s phone with TMS access gets lost?
Modern TMS platforms like Omniful support remote logout and can revoke access instantly via admin panels.
Can a TMS support KSA’s data residency laws?
Yes. Omniful’s TMS is compliant with Saudi data hosting rules and offers localised infrastructure.
How do I know if my TMS is compliant?
Request documentation on certifications, conduct audits, and ensure vendors provide SLAs that include security coverage.
Final Thoughts: Don’t Trade Speed for Security
Efficiency and scale should not come at the cost of privacy. A robust TMS system should help you move faster and smarter — not make you vulnerable.
For MENA businesses navigating a hypercompetitive landscape with digital-first expectations, securing transportation data is now a strategic priority. Choose solutions like Omniful’s Transportation Management System that align with local regulations and global best practices.
When you protect your data, you protect your customers, your brand, and your future.